Anatomy of a Ransomware Attack
Anatomy of a Ransomware Attack
A cyber extortion attack is never just a cyber extortion attack. There is always an escalation in activities from the adversary’s initial entry, expansion throughout the environment, and ultimately the extortion threat.
While every attack is different, there are common adversary activities associated with most, if not all, cyber extortion attacks. Understanding these common threads can help victims more effectively respond to cyber extortion attacks, minimize damage, and in some cases, prevent extortion from occurring in the first place.
In this chapter, we deconstruct a cyber extortion attack into key components and present these along with common indicators of compromise and effective response tactics.
3.1 Anatomy Overview
Cyber extortion attacks do not begin and end with the extortion demand itself, although this is often the most visible part. The authors of this book have analyzed hundreds of extortion cases, many firsthand, and identified common adversary tactics observed throughout these attacks. A visual representation of this anatomy is shown in Figure 3.1.
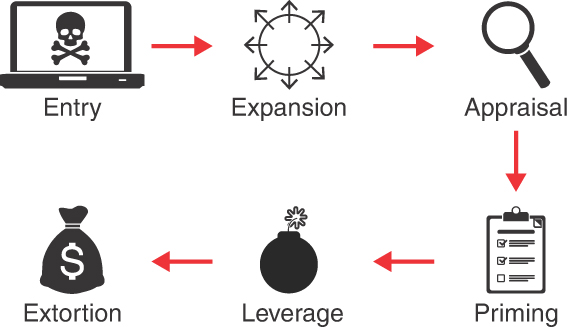
Figure 3.1 Anatomy of a cyber extortion attack
(Illustration courtesy of LMG Security. Graphics: computer, grmarc/Shutterstock; skull and crossbones, Sergey Siz`kov/123RF; circle with arrows, bloomua/123RF; magnifying glass, olesya k/Shutterstock; clipboard, HSDesain/Shutterstock; bomb, AcaG/Shutterstock; money bag, Pensiri Saekoung/123RF)
Importantly, cyber extortion attacks are not a linear process. An adversary may cycle through various components multiple times, or even repeat the entire process as part of a single overarching attack.
The common components of cyber extortion attacks include:
Entry: The adversary gains unauthorized access to the victim’s information technology resources.
Expansion: The adversary engages in a recursive process of expanding access. During this phase, the adversary typically gains persistence, conducts reconnaissance, increases the scope of their access, and transfers access to other adversaries.
Appraisal: The adversary assesses the victim’s strengths and weaknesses, including data repositories, financial posture, operational infrastructure, and more. This information is used to define and refine the adversary’s ongoing attack strategy.
Priming: The adversary modifies the environment to maximize leverage in the following phases. This may include destroying backups, dismantling security, monitoring systems, and more.
Leverage: The adversary actively threatens the confidentiality, integrity, or availability of the victim’s information resources. This is commonly accomplished by detonating ransomware, exfiltrating data to systems under the adversary’s control, launching a denial-of-service attack, or all of these.
Extortion: The adversary demands payment or services in exchange for restoring availability, integrity, or confidentiality of data or technology resources.
In the following sections, we discuss each of these components in detail, highlight opportunities for early detection, and discuss effective response strategies.
3.2 Entry
In the entry phase, the adversary gains a foothold inside the victim’s technology environment.
While this may mean that the adversary gains access to a computer inside the victim’s network, it could also be a cloud-based resource such as a virtual machine, a hosted application such as email, or a remote system such as an employee’s personal computer.
Whatever the point of entry, the adversary will leverage this initial access during the next phase (expansion) to spread throughout the environment.
Common methods of entry include:
Phishing: The adversary sends an email, text, or other message designed to trick the victim into taking an action that gives the adversary information and/or access to the victim’s environment.
Remote logon: The adversary successfully gains access to an interactive session via a remote logon interface such as Remote Desktop Protocol (RDP), using credentials that have been guessed, stolen, purchased, or otherwise obtained.
Software vulnerability: A vulnerability is found in the victim’s Internet-facing applications, servers, or network equipment.
Technology supplier attack: The adversary has access to a supplier’s technology resources (such as a software provider or managed service provider [MSP]), whether legitimately or through compromise, and leverages this to gain access to the victim’s environment.
Let’s discuss how adversaries execute each entry method, and highlight the corresponding opportunities for detection and effective response techniques.

3.2.1 Phishing
Cyber extortion events often start with a phishing attack, in which the adversary sends a message designed to trick the intended victim into taking an action, such as clicking on a link or opening an infected attachment.
Phishing kits, which automate the attack process, often sell for $5 to $15 on the dark web.
Phishing attacks can be conducted via any form of messaging, from email to SMS messages to social media. (Carrier pigeon, anyone?) However, cyber extortionists typically aim to get a foothold within an organization’s network, and email is the most widely used method for transmitting messages from external to internal senders in these types of environments.

3.2.1.1 Remote Access Trojans
The payload of phishing messages is often a remote access Trojan (RAT), which is a software utility designed to enable an adversary to remotely control or access a computer system.
The features of RATs vary widely, but typically they enable an adversary to do the following:
Establish a communication channel between the compromised endpoint and a controlling server
View data about the infected computer
Control the infected computer remotely
Evade detection
Sophisticated RATs can include advanced capabilities, enabling the adversary to take the following steps:
Automatically steal sensitive information from the victim’s computer, such as credit/debit card numbers, stored passwords, computer system information, and more
Interactively log on using Virtual Network Computing (VNC) or a similar program
Produce reports of user activity, account balances, web history, and more
Execute advanced privilege escalation attacks and facilitate the adversary’s lateral movement
Install addition malware (including ransomware)
Leverage the victim’s computer(s) to attack other organizations
Malicious Swiss Army knives such as Emotet and Trickbot rely on phishing campaigns to deliver their malware, which adversaries leverage to gain persistent access, steal information, and distribute other threats.
The presence of a RAT is often a precursor of a cyber extortion attack.
Traditionally, RATs are delivered via social engineering attacks such as phishing emails, malicious websites, or compromised applications.
The adversary who installs a RAT may conduct cyber extortion, or sell or rent access to other criminals, who in turn may choose to conduct cyber extortion themselves.
Opportunities for Detection
When an extortion attack starts with phishing, typically a user device is “patient zero,” the first system entered by the adversary. From there, the adversary establishes persistence, which typically involves a reverse shell of some kind (since most devices are blocked by the firewall from direct inbound Internet access). The adversary then leverages stolen credentials or unpatched vulnerabilities to escalate their account privilege, move laterally, and spread throughout the environment.
Specific indicators include the following:
Warnings and alerts in email security software: In some cases, the suspicious email may be automatically quarantined; in others, the email is sent along with a warning to the users, email administrator, or both. The user’s email system may also insert a warning in the subject or body of an email if the email meets certain criteria that are in line with characteristics of a phishing attack.
User report: A user may report the phishing message to the response team. When this happens, IT staff should quickly look for other users who received the same or similar phishing emails and remove those emails from other users’ inboxes. If any user clicked on a link or attachment in the suspected email, this should activate the organization’s incident response processes to ensure that any resulting infection is contained.
Malware sample: By analyzing a malware sample, you can often match it to specific known phishing campaigns or hacker groups and obtain lists of additional indicators to search for in the affected environment.
Email application logs: Application logs may contain warnings related to emails that have been processed, or alerts on blocked attempts, which can help you identify high-risk users, periods of unusual activity, changes in user risk profiles, and more.
Antivirus log entries: When a user clicks on a link or attachment in a phishing email and downloads or runs malware, it may generate an antivirus software alert.
Event logs: Similarly, when a user clicks on a link or attachment in a phishing email that results in code execution, it may generate records of unusual activity such as privileged command execution, scheduled task creation, or application and service starts or stops.
3.2.2 Remote Logon
Many cyber extortion attacks occur because the adversary gained access to a remote logon interface, such as an RDP platform. Quite often, cyber extortionists purchase stolen credentials on the dark web from an initial access broker rather than stealing or guessing them.4 Then, the extortionists use these credentials to gain a foothold in the network and deploy their attack.
There are good reasons why “open” RDP services have traditionally been the root cause of a large percentage of extortion attacks:
No special tools are needed to gain remote access to the service.
RDP is a common protocol that often does not trigger alerts, particularly if it is actively used by employees or an IT administrator.
The adversary can often pivot through the compromised computer to gain access to other systems using RDP inside the network.
Many organizations use RDP or other remote access tools so that employees can log in to their workstations from home or while traveling, or so IT administrators or vendors can access an internal network remotely at all hours. This is also—and unfortunately— convenient for adversaries, who frequently steal credentials or use password-spraying attacks to gain unauthorized access.
The vast supply of stolen passwords available for free or for sale on the dark web has fueled these attacks. By the summer of 2020, researchers had identified more than 15 billion stolen username and password combinations on the dark web. At the time of this writing, stolen RDP credentials sell for $16 to $24 each.
Many people reuse the same password for multiple accounts.7 Adversaries leverage this tendency by conducting “credential stuffing” attacks, in which they take stolen credentials and attempt to use them on a wide variety of logon interfaces. When they successfully log in to another account, they can either leverage it themselves or sell access to the newly compromised account.
In 2020, the COVID-19 pandemic suddenly created a rush to remote work. In response, many organizations rapidly enabled remote access with little security oversight, and were compromised as a result.
Opportunities for Detection
Common signs of remote authentication attack or compromise include the following:
Failed logon attempts: When an adversary conducts password spraying or credential stuffing attacks, there are often repeated failed logons (sometimes followed by a successful logon). This can occur at the perimeter, or it can occur within the network as the adversary attempts to move laterally. Unfortunately, many networks are not configured to record or report failed logon attempts on Microsoft Windows hosts within their network, meaning that an adversary can automate attempts to authenticate within the network without being detected.
Unusual successful logon attempts: These may include logins at odd times or places, distinct user-agent strings, and “impossible travel” alerts notifying of logons from geographically distant locations in a quick succession.
Creation of new accounts: Such accounts may suddenly be used for remote access.
3.2.3 Software Vulnerability
Adversaries routinely search for exploitable vulnerabilities in widely used software and leverage these to launch cyber extortion attacks, as seen in the Kaseya attacks, as well as adversaries’ response to the ProxyShell and Log4j vulnerabilities (among many others).
In the case of Accellion, the Cl0p group was able to exploit a critical vulnerability in Accellion FTA devices and steal sensitive data affecting more than 9 million individuals, resulting in a $8.1 million class-action settlement in January 2022.8
The “Shodan.io” search engine, which indexes Internet-connected devices, can be used by adversaries and defenders alike to identify potentially vulnerable Internet-facing services.
Timely patch deployment can dramatically reduce the risk of a perimeter device compromise.
However, IT administrators are often unaware that their specific firmware or software version is vulnerable, particularly in organizations that have limited resources for IT management.
Furthermore, zero-day vulnerabilities exist for perimeter devices, and may be incorporated into high-end exploit kits before the manufacturer has time to identify the issue.
Opportunities for Detection
Common signs of attack via perimeter software vulnerability include the following:
Alerts on port or vulnerability scans on perimeter devices (although this is a normal occurrence, so it’s important to review such alerts carefully and resist the urge to be lulled into complacency)
Strange error messages relating to that application or system, performance degradation (processes that overwhelm the processor or memory), or system/application crash
Unexpected outbound connections from servers or even workstations
Unusual and unrecognized processes or applications running on perimeter systems
3.2.4 Technology Supplier Attack
Frighteningly, the entry point for a cyber extortion attack may be a supplier, such as an IT provider, MSP, equipment vendor, or cloud provider. In 2019, 22 towns in Texas were hit with a devastating REvil ransomware attack, which was traced back to their common MSP.
After infiltrating the MSP’s network, the adversary leveraged the MSP’s normal remote administration tool, ConnectWise Control, to deploy the ransomware throughout customer networks.
Thanks to an effective backup and recovery strategy and strong response plan, the towns’ operations were successfully restored within a week.10
Cloud providers, too, suffer ransomware attacks that can dramatically impact customers.
In May 2020, Blackbaud, a leading provider of cloud-based fundraising software, was hit with a ransomware attack.
Customers were notified in July and told that “the cybercriminal removed a copy of a subset of data from our self-hosted (private cloud) environment … we paid the cybercriminal’s demand with confirmation that the copy they removed had been destroyed.”
Blackbaud’s ransom payment was little consolation to the thousands of customers who stored sensitive data in the cloud, many of whom were required to conduct their own investigations—often at their own expense.
Without direct access to evidence, however, their response was hampered.
Within just a few months, Blackbaud had been sued in 23 proposed class-action lawsuits, received approximately 160 claims from customers and their attorneys, and been hit with inquiries from a plethora of government agencies and regulators.
Opportunities for Detection
Customers typically have little visibility into the operations and risk management practices of suppliers, even those that have a high level of access to their sensitive data or network resources.
They also have no way to directly detect an intrusion into supplier networks and must rely on suppliers to implement effective detection capabilities to prevent the spread of ransomware.
Visible signs of a supplier compromise may include the following:
Unusual logins or activity from supplier accounts
Spam emails originating from a supplier’s address
Unusually slow service or full outages
Notification or media reports of a cybersecurity compromise relating to the supplier
3.3 Expansion
Once an adversary gains access to the target’s technology resources, typically they engage in a recursive process in which they establish persistence, conduct reconnaissance, update their attack strategy, and broaden their access. These activities build off each other and often occur at the same time, rather than in a clear linear progression, as illustrated in Figure 3.2.
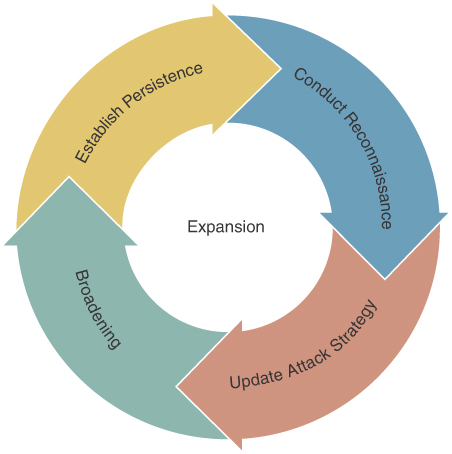
Figure 3.2 The “expansion” phase of a cyber extortion attack
Activities at this stage include the following steps:
Establish persistence: The adversary works to establish sustained, reliable access over an extended period of time and evade detection. To accomplish this, the adversary may install remote access tools, neutralize antivirus software, add new accounts, and so on.
Conduct reconnaissance: The adversary gathers information that will enable them to expand the scope of compromise. This may include network mapping, password cracking and interception, and more.
Update the attack strategy: The adversary uses the information gleaned to refine their goals, plan, and processes.
Broadening: The adversary increases their access to systems, accounts, or other network resources, by escalating privileges, moving laterally through the network, and gaining access to different applications and technology resources.
Along the way, all of the adversary’s activities provide defenders with opportunities to detect and eradicate the threat.
Each interaction generates unique and identifiable indicators that a security team can monitor to identify the threat.
In particular, during the early stages of an attack, the adversary is at their most vulnerable, since they are likely still unfamiliar with the network topography and may unwittingly create “noise” while engaging in network reconnaissance and other expansion activities.
The method of access and the adversary’s skill set can also vary significantly, leading to variations in IoCs and detection strategy.
In the following sections, we describe specific indicators of compromise that can facilitate detection and enable defenders to break the chain of attack.
3.3.1 Persistence
Simply gaining access to a victim’s network once is not usually sufficient to gain extensive leverage over a victim.
Instead, the adversary must find a way to access resources on the victim’s network repeatedly over a sustained period of time.
Frequently, the adversary lurks on the network for an extended period of time (even weeks or months) prior to gaining leverage (e.g., exfiltrating data, detonating ransomware).
This means that the target has an opportunity to detect and eradicate the compromise before the worst occurs.
Opportunities for Detection
The specific indicators of compromise vary based on the method of access, but almost universally, the adversary needs to generate periodic network traffic.
They often use a command-and-control server, otherwise known as a C2 server, in which an infected endpoint “phones home” to an adversary-controlled server.
They may also use standard IT remote access tools such as RDP, Anydesk, or others.
Defenders should be on the lookout for telltale signs of suspicious network activity:
Suspicious source/destination IP addresses and domains
Network communication originating from unfamiliar or unexpected processes
Malformed communications—for example, DNS requests with Base64 encoded content instead of normal URLs
Unauthorized remote access attempts
3.3.2 Reconnaissance
Now that the adversary has established a consistent method of entering the environment, they will often perform information gathering tasks to better understand the network, its connected devices, and potential targets for further exploitation.
The adversary can perform these activities using built-in system tools, third-party software, or both.
The adversary will often look for the following items:
Local IP address range information
Available subnets
Domain information
Available network services
DNS information
Using information gathered from the network, the adversary can effectively map the environment they now have access to and determine their best options for additional actions after the initial compromise.
Additionally, because system administrators often include function descriptions in network computer names (i.e., Fileserver-01 or DC-01), the adversary can specifically target anything that they identify as a potentially high-impact target.
Often, indicators of network reconnaissance are observed during the early stages of an incident.
This provides an opportunity to greatly reduce an adversary’s ability to spread through the network or possibly stop it entirely.
Opportunities for Detection
The following indicators can signal potentially malicious network reconnaissance:
Indicators of port scanning (NMAP)
Increased network resource usage from suspicious computers
Outbound network traffic spikes at irregular hours
Increased outbound network traffic
3.3.3 Broadening
Once the initial foothold is secured, the adversary works to expand access to additional network resources, including high-value systems that hold confidential information or can be used to control resources.
Along the way, the adversary will attempt to gain additional privileges, specifically targeting domain administrator privileges and administrative access to cloud tenants/applications.
Typically, the adversary’s activities include at least the following:
Privilege escalation: The adversary attempts to gain a higher level of user privileges. In the early stages, this is often accomplished by scraping credentials from system memory using a tool such as Mimikatz, extracting saved passwords from web browsers, capturing Kerberos tokens, or simply searching the infected host for documented credentials. Once the adversary has moved laterally throughout the network, they may engage in more sophisticated privilege escalation attacks involving theft of private keys, Security Assertion Markup Language (SAML) token forgery, and more.
Lateral movement: The adversary attempts to gain access to other hosts on the network by using stolen passwords, exploiting vulnerabilities, or applying other tactics. Commonly, this process is facilitated by the widespread practice of configuring a static local administrator password shared by all endpoints.
Application/cloud access: The adversary accesses applications and cloud tenants, typically by using stolen passwords or leveraging trust relationships between local systems and services.
If an adversary is able to establish a significant breadth of access, it becomes much more difficult to fully eradicate the threat.
Opportunities for Detection
Common indicators of broadening or expanding access by adversaries include the following:
Unusual Local Administrator account activities, including network authentications or shared folder access
Connections to core assets from unusual or unauthorized workstations
Suspicious application access
Impossible travel alerts
3.4 Appraisal
Once inside a victim’s environment, adversaries often explore and identify any valuable data. This can include information that is useful for the following purposes:
Applying pressure in extortion: The adversary can use regulated data such as electronic protected health information (ePHI) or Social Security numbers to remind the victim of the potential for fines, regulatory investigation, or other government actions. In some cases, victims may store direct contact information for data subjects, whom adversaries can contact and attempt to intimidate.
Setting a ransom demand: Financial details and cyber insurance coverage can inform the amount of the adversary’s ransom demand.
Sale: Intellectual property and personally identifiable information (PII) are valuable information that can be sold to third parties.
The adversary may update their attack strategy based on these findings. This may include determining whether to install ransomware, identifying information to exfiltrate, setting a ransom demand, and more.
Opportunities for Detection
Look for the following indicators that an adversary may be appraising your infrastructure (among others):
Unexpected or unauthorized access to files. Typically this is identified using third-party security software or security information and event management (SIEM) conditional alerting.
Last read/modified dates on files that are more recent than expected.
Forwarded or copied emails containing information about insurance coverage, finances, and so on.
3.5 Priming
Prior to gaining leverage, the adversary will typically “prime” the environment to maximize the potential damage and impact.
For example, before detonating ransomware, the adversary may modify key network configuration settings and disable antivirus software.
These steps are intended to remove roadblocks and improve the chances of a successful detonation during the next stage of the attack.
Adversaries commonly modify and/or disable the following network components:
Antivirus/security software
Processes and applications
Logging/monitoring systems
Filesystem permissions and configuration
In the remainder of this section, we discuss each of these in turn.
3.5.1 Antivirus and Security Software
Security and antivirus software present hurdles for adversaries and can issue alerts during any phase in the compromise.
Signature-based antivirus software may detect and delete the malicious files used by the adversary, or heuristic security software may detect the actions associated with file encryption and stop the process before it completes.
As a result, neutralizing security software is often a top priority for the adversary. Typically, this will take the form of one or more of the following actions:
Disabling security software: If the adversary is not worried about making too much noise on the network, a common tactic is to simply disable the active security software currently in use by the victim by killing the active process. This can prevent the software itself from alerting, but it can also set off alerts within the victim’s network notifying IT security personnel that something is wrong.
Modifying configuration: In some cases, an adversary may gain access to the centralized console used to manage a security application. If the software allows for global changes, the adversary may modify the configuration so as to neutralize the software across the entire domain. For example, often the adversary will put the security software into a “monitor-only” mode, allowing the adversary to freely distribute malware without interference.
Allowlisting signatures: An adversary with sufficient access may simply allowlist signatures associated with their specific malware in the victim’s security software. Like service alteration, this type of change requires access to a central administration platform but will rarely generate an alert from the software itself. While not the most common method of evasion, signature exceptions can often be nearly invisible to the victim.
Opportunities for Detection
The following indicators suggest that security software on your network may be under attack:
Alerts for nonresponsive antivirus software on endpoints
State-change alerts from security software
3.5.2 Running Processes and Applications
Many software applications are designed to prevent other services from modifying open files or databases while they are in use, thereby minimizing the risk of corruption.
This is especially common in software that maintains a database, such as a SQL server application or a financial application like QuickBooks.
One unexpected silver lining is that these applications may inherently block ransomware from encrypting important databases and files if they are actively in use.
Opportunities for Detection
How can you recognize that an adversary may be actively compromising services and applications on your network? Look for the following indicators:
System health indicators, which you can use to flag modifications of this type
Signature identification of tools such as ProcessHacker
3.5.3 Logging and Monitoring Software
Event logging and monitoring software can enable victims to:
Detect anomalous activity quickly and thwart the adversary
Trace the adversary’s activities through the network and close any security gaps
Quickly eradicate the adversary from the network
Gain information that could be leveraged in a negotiation
As a result, adversaries often take steps to undermine event logging and monitoring capabilities.
Without accurate logging, activities including access times, filesystem exploration, indicators of exfiltration, and other valuable information may no longer be available.
Many small and midsized organizations rely on local log files on the affected host, and do not have a central SIEM, which makes the adversary’s job easier.
Often, adversaries will undermine event logging and monitoring using the following tactics:
Log deletion: The adversary may delete key elements of the available log data to completely obscure local system activities. These sources of data commonly include Windows Event Log data, Link files, Jump lists, Windows Explorer history, web browser history, and more.
Stop services: If a log collection service like Winlogbeat or Rsyslog is in use to centralize log collection, the adversary may simply kill the export service on the local system, effectively stopping the collection of data.
Time-stomping: The adversary may alter timestamps on log data to make investigating the attack and correlating logs between multiple systems difficult, if not impossible. This may also be done to obscure the identification of files or programs used in the attack.
Opportunities for Detection
The following evidence suggests that logging and monitoring solutions have been tampered with:
Event log data indicating that logs have been cleared (i.e., Event ID 1102 on a Windows host)
Use of a specialized utility such as the Sysinternals SDelete tool to make deleted log recovery impossible
Alerts for data stoppage from monitored hosts
3.5.4 Accounts and Permissions
To ensure an effective rollout of ransomware encryption software, the adversary typically adds at least one account and carefully modifies access permissions to ensure that the ransomware spreads as quickly and effectively as possible. Here are some specific, commonly used tactics:
Create new administrative user accounts: By the time the adversary is in the “priming” phase, they usually already have domain administrator access. However, the adversary will typically create a different account to use for the ransomware deployment. This will make it more difficult for the victim to trace the attack back to the actual accounts that the adversary used prior to detonation.
Add the account to the “remote users” groups: This gives the newly created user access to all endpoints that have remote access enabled.
Gain unauthorized network share access: This enables the ransomware to encrypt shared drives and connected devices (including, much of the time, backups).
Perform unauthorized software installations: The adversary uses common administrative tools (such as PsExec) to automate deployment of the ransomware.
Opportunities for Detection
Set up logging and automated alerts for the following indicators:
New or unknown administrative user accounts
Increases in remote connection activity or unusual accounts accessing remote services
Unauthorized access to network shares
Installation of unauthorized software
3.6 Leverage
To actually launch an extortion attack, the adversary first needs to gain leverage by actively threatening the confidentiality, integrity, and/or availability of information resources.
Most commonly, adversaries accomplish this by encrypting files with ransomware, or stealing sensitive data so they can later threaten to publish it if they do not receive payment.
In this section, we discuss the two most common scenarios: ransomware detonation and data exfiltration.
Keep in mind that these are only selected examples—there are many other ways for adversaries to gain leverage over a victim. Ultimately, adversaries are limited only by their imaginations.
3.6.1 Ransomware Detonation
The detonation phase represents the last piece of “hands-on” access that an adversary will normally execute.
Once the adversary has mapped their targets, obtained sufficient access, and potentially exfiltrated everything they want, the final fireworks show at the end of the incident is the detonation of a ransomware executable.
This phase of the attack is often the first indicator of compromise a victim sees directly and, unfortunately, at this point it is usually too late to prevent the attack.
An adversary can distribute and detonate their encryption software in many different ways. Here are three common methods:
Group policy: An adversary with access to a domain controller and domain administrator credentials can use the software distribution system built into most Windows networks as a springboard to distribute their malicious software. This activity is typically accompanied by the creation of a scheduled task that can simultaneously detonate the ransomware payload on all computers within the victim’s environment. This shortens the overall period in which a defender could stop the attack, and also makes investigating the attack more difficult because it can effectively obfuscate the origin of the malware execution.
System administration toolkit: Adversaries are frequently observed using the PsExec toolkit or similar utilities to distribute their malicious payload. Configuring a network to accept this type of software push is trivial, and the previous expansion steps taken by the adversary usually provide them with exactly what they need to initiate this form of detonation. The PsExec utility is part of the Microsoft SysInternals toolkit and automates the process of distributing executable programs to domain-connected hosts.
Manual distribution and detonation: In some cases, the adversary may choose to avoid automated distribution and simply install and execute the encryption software manually on selected targets within the overall network. This tactic is observed in both small networks with a minimal number of overall targets and large organizations. In the latter case, an adversary is more concerned with encrypting the “crown jewels” of the network than with encrypting every individual host.
Once the ransomware payload is detonated, the exact sequence of events varies depending on the strain. However, there are some common actions that the software typically executes:
Adds malicious software to startup sequences, which facilitates persistence between reboots.
Creates ransom notes.
Deletes shadow volume copies, to prevent file restoration.
Enumerates drives, often starting with drive A:\ and moving alphabetically through the hosts’ mapped drives.
Encrypts files. Most ransomware strains encrypt a targeted list of files, often based on a preloaded list of file extensions.
Encrypts backup files once found on the network.
Opportunities for Detection
While some might seem obvious, here are the signs indicating that ransomware has been detonated on a network:
Unauthorized software installations
Unauthorized or unusual scheduled task creation
Registry modification
Visible ransom notes
Encrypted files
3.6.2 Exfiltration
The adversary may deliberately exfiltrate data to use it as leverage in extortion, commit fraud, or sell it.
This type of exfiltration is distinct from the network reconnaissance discussed in Section 3.2.3, in that the purpose is to gain some benefit beyond simply increasing access.
For example, the Conti playbook that was leaked in 2021 (discussed in Section 2.9.6) illustrated how adversaries now purposefully search for financial documents, accounting information, client data, and more.
The adversaries also seek out details that are specifically useful for negotiating extortion payments, such as cyber insurance policies. Today, this has become standard practice, and the exfiltration often occurs quickly and in bulk.
Adversaries could exfiltrate data from any repository, including systems on a local network, mobile device, or cloud repository. In today’s cloud-driven technology landscape, sensitive data is often stored via Amazon S3, Dropbox, SharePoint, and other cloud-based storage systems.
Adversaries often access the data held within the cloud using credentials and access keys obtained during their takeover of their victims’ local network, and vice versa.
Because the adversary might transfer or sell access to the victim’s technology environment at any point, it is entirely possible for a victim’s data to be stolen multiple times by different adversaries.
Adversaries commonly use the following tools for exfiltrating data:
Mainstream cloud services: The advantage of these services—which include Dropbox, Google, OneDrive, and others—is that they are often already supported by the local environment and can blend with normal usage.
File transfer programs: The adversary can use common Windows utilities such as WinSCOP or Powershell to send data to a server under their control. Typically the data is encrypted or encoded in transit.14
Anonymous file sharing services: MEGA, FreeFileSync, and similar services are very convenient aids for adversaries, since they require little effort to set up and are free up to a certain volume of data. MEGA has become particularly popular. It includes built-in end-to-end encryption, making it difficult for data loss prevention systems to detect, and the user can transfer files using a web browser or desktop app. Since these services are not normally used in a standard enterprise environment, it can be easy to detect and block applications of this type.
Three data exfiltration patterns are commonly seen in cyber extortion cases:
Automated RAT exfiltration
Mass repository theft
Curated theft
Each of these exfiltration patterns leaves a different footprint in the network and may require different response tactics. In the following subsections, we discuss each in turn.
3.6.2.1 Automated RAT Exfiltration
Quite often, a RAT installed on the victim’s network is configured to automatically steal files and upload them to a system controlled by the adversary.
When this occurs, the RAT typically has a configuration file that allows the operator to select files based on an extension and/or keywords in the filename.
For example, the authors of this book studied one widely used RAT, Atmos, which shipped with a default configuration that exfiltrated all files with .pdf and .docx extensions, plus any documents containing the keywords “bank” or “payroll” in the filename.
In this case, as in many others, the adversary’s goal was likely to facilitate financial fraud.
Modern RATs are sophisticated and typically include built-in techniques to help the user avoid detection.
When files are automatically exfiltrated, typically the data transfer is slowly metered so that it doesn’t set off network monitoring alerts.
RATs typically transfer data over the built-in command-and-control channel, which is often encrypted, again for evasion purposes.
Although the functionality of RATs varies, the data normally winds up on a server under the adversary’s control—often another hacked server that is part of a botnet.
Depending on the RAT’s level of sophistication, the adversary may even have point-and-click access to view and sort stolen files through the RAT’s interface.
3.6.2.2 Mass Repository Theft
Today, “smash-and-grab” data exfiltration is a popular technique. Many adversaries enter the network with the goal of stealing data, and invest little time in curation before theft.
Why bother sorting through the data while on the victim’s network, when the adversary can steal it en masse and analyze it on their own systems?
In cyber extortion cases, typically there is no need to pick through data extensively to accomplish the adversary’s objectives.
Once the adversary has access to the victim’s network, they seek out large data repositories and transfer them out in bulk. Then, during the negotiation phase, they can share screenshots of the stolen data or provide file lists.
No matter if the bulk of the stolen files is unimportant; the presence of even a few documents containing PII can spell reputational disaster for the victim.
In some cases, bulk file transfer can cause significant headaches for the victim.
Once the victim is aware that data may have been stolen, typically the next step is to take an inventory of the potentially exposed data and create a notification list.
Firms that conduct e-discovery normally charge by the gigabyte, so even if the majority of the stolen files contain no sensitive data, the cost for verifying this fact may be large.
In some cases, the adversary “stages” data on a single system prior to exfiltration.
This process gives the adversary time to organize files, ensure everything is compressed and encrypted, and then exfiltrate it all at once, giving the victim limited time to respond before all the data flies out the door.
The Lockbit extortion gang was observed staging data and organizing files based on the system from which they were stolen, and then copying the directories to a single MEGA console before uploading them. However, quite often adversaries do not bother “staging” data at all, but simply copy it directly from the hacked systems.
As RaaS kits become more automated, adversaries are curating less and automatically exfiltrating data more.
The Netwalker RaaS platform advertised “[a] fully automatic blog, into which the merged data of the victim goes, the data is published according to your settings.”
The RaaS automatically exfiltrated the victim’s data to MEGA, and then created a blog where the MEGA links would appear at the proper time.
3.6.2.3 Curated Theft
In some cases, an adversary may steal only specific files of value, such as source code, databases of PII, or other material.
To accomplish this, the adversary needs to first identify these files on the network, typically through manual examination.
Often, content of this type is curated due to the size of the repository, or because the attack is targeted and the adversary has a predetermined goal in mind.
For example, the gaming company CD Projekt Red was hit with a ransomware attack in 2021, when adversaries specifically leveraged stolen source code in their ransom note.
“We have dumped FULL copies of the source codes from your Perforce server for Cyberpunk 2077, Witcher 3, Gwent and the unreleased version of Witcher 3!!!”17
Due to the size of the source code repositories, and the fact that these were stored in the dedicated Perforce software, exfiltration of this material was undoubtedly purposeful and curated.
The adversary also explained that they had stolen materials relating to accounting, human resources, and more, but specifically leveraged the intellectual property in their extortion efforts.
“If we will not come to an agreement,” they threatened, “then your source code will be sold or leaked online, and your documents will be sent to our contacts in gaming journalism.”
Opportunities for Detection
Signs of data exfiltration may include the following unexplained or unusual activities:
Increases in network traffic, particularly outbound direction
Connections to cloud file sharing services
Use of MEGA and other third-party file sharing websites that are not typically used
File movement and staging activities
Connected sessions with unknown or suspicious destinations
3.7 Extortion
The final phase of a cyber extortion incident is often the loudest and most aggressive.
The adversary has already taken the time to infect the network, compromise assets, exfiltrate data, and/or encrypt the filesystem, and now the adversary is looking to monetize the attack.
With the need for stealth gone, the adversary begins the process of extortion. The primary extortion notification methods typically include:
Passive notification (i.e., the ransom note)
Active notification (e.g., phone calls, voicemails)
Third-party outreach (e.g., direct communications with customers, data subjects)
Publication (e.g., dark web blogs, Telegram channels, Twitter feeds)
We discuss each of these tactics in turn in the following subsections.
3.7.1 Passive Notification
The adversary typically makes it obvious to the victim that they are being extorted.
This can be, and often is, as simple as a ransom note left on the desktop. However, many adversaries have leveled up, and now include multimedia such as audio versions of the ransom demand.
The ransom note commonly includes the following information:
An announcement of what happened
Instructions for how to recover files
A clear deadline (this may be a countdown timer or a simple deadline)
Contact information for the adversary (typically an email address or link to a portal)
Advice for obtaining cryptocurrency
Psychological pressure, such as threats (e.g., “Your business is at serious risk.”) as well as reassurances (e.g., “But do not worry. You have a chance! It is easy to recover in a few steps.”)
Figure 3.3 shows an example of a ransom note left by the Maze hacking group in 2020.
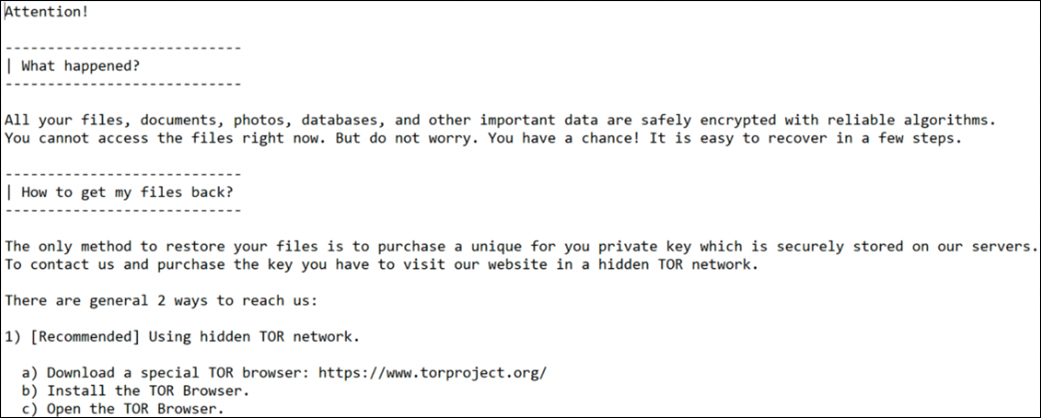
Figure 3.3 A sample Maze ransom note from the LMG Security malware lab
(Illustration courtesy of LMG Security)
3.7.2 Active Notification
The adversary might actively engage in communicating with the victim throughout the extortion phase.
This commonly includes sending emails, but can also involve phone calls, text messages, voicemails, Telegram messages, and other methods.
Typically, the aim is to intimidate the victim and demonstrate the adversary’s level of access. In many cases, adversaries monitor the victim’s emails and may even make snide comments on current response activities.
3.7.3 Third-Party Outreach
Adversaries have been known to reach out directly to third parties affected by the compromise, including customers, patients, data subjects, and business associates, to encourage them to pressure the victim organization into paying a ransom. In some cases, they may also reach out to competitors or others in an effort to sell stolen data.
As discussed in Section 2.7, The Dark Overlord (TDO) cyber extortion group hacked the Johnston Community School District Iowa in 2017 and texted threatening messages to parents. More recently, cyber extortion gangs have taken to leveraging scalable communications methods such as email so as to connect directly with data subjects and affiliates. For example, one convenience store chain that was extorted by the Clop ransomware gang discovered that its customers had received the following email notifying them of the compromise:
Good day!
If you received this letter, you are a customer, buyer, partner or employee of [VICTIM- REDACTED]. The company has been hacked, data has been stolen and will soon be released as the company refuses to protect its peoples’ data.
We inform you that information about you will be published on the darknet (http:// ) if the company does not contact us.
) if the company does not contact us.
Call or write to this store and ask to protect your privacy!!!!
3.7.4 Publication
Adversaries may publish extortion notification on dark web sites, Telegram channels,23 social media platforms, and more, anticipating that victims will view their posts and receive pressure from third parties. In addition, adversaries routinely leverage the mainstream media, particularly when threatening to publish data, as discussed in Section 2.8.
3.8 Conclusion
In this chapter, we stepped through the anatomy of a cyber extortion attack, including each of its components: entry, expansion, appraisal, priming, leverage, and extortion. Along the way, we described the adversary’s activities in depth, and provided indicators of compromise that can help responders identify these activities.
In the next chapter, we will discuss the initial response once an intrusion has metastasized into a cyber extortion attack.
3.9 Your Turn!
Every cyber extortion incident is unique. The response team’s options and priorities will vary depending on the victim organization’s industry, size, and location, as well as the details of the incident itself.
Based on what you learned in this chapter, let’s think through key elements of a cyber extortion attack.
Step 1: Build Your Victim
Choose one characteristic from each of the three columns to describe your victim’s organization:
Industry | Size | Location |
|---|---|---|
Hospital | Large | Global |
Financial institution | Midsized | United States |
Manufacturer | Small | European Union |
Law firm |
| Australia |
University |
| India |
Cloud service provider |
| Country/location of your choice |
Organization of your choice |
|
|
Step 2: Choose Your Incident Scenario
Select from one of the following incident scenarios:
A | Ransomware strikes! All of the victim’s files have been locked up, including central data repositories, servers, and workstations. |
B | A well-known cyber extortion gang claims to have stolen all of the victim’s most sensitive data and threatens to release it unless the victim pays a very large ransom demand. The gang posts the victim’s name on their dark web leaks site, along with samples of supposedly stolen data. |
C | Double extortion! Both A and B occur at the same time. |
D | The victim is hit with a denial-of-service attack on their Internet-facing infrastructure that slows their access and services to a crawl. The adversary threatens to continue and even escalate the attack unless a ransom is paid. |
Step 3: Discussion Time
Your victim organization has experienced a cyber extortion event. Given what you know about the victim and the scenario, answer the following questions:
Should the victim organization assume that the extortion demand was the adversaries’ only activity relating to their environment? Why or why not?
Name the steps that adversaries often take in the leadup to cyber extortion.
Describe at least one way that the victim can often detect early signs of this type of attack prior to the extortion phase.
What are the most common methods of entry that the victim organization should check for?
Which means might the adversary use to try to notify the victim of the extortion demand?
























